Cybersecurity Data Flow Diagram Cyber Security Flow Chart
Cyber security flow chart Cyber security: a paradigm shift in it auditing Pin on cybersecurity
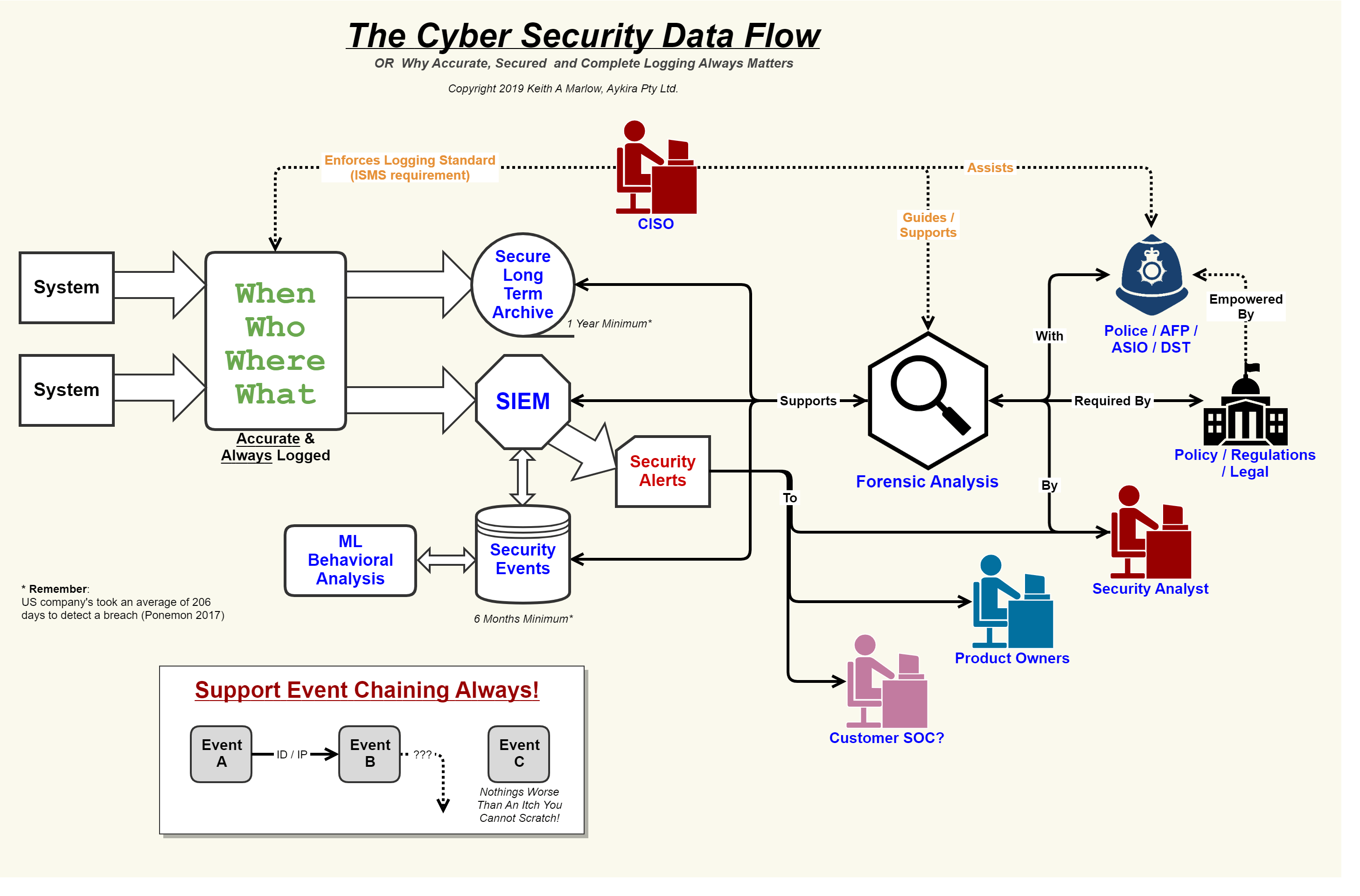
Security Event Logging, why it is so important – Aykira Internet Solutions
Simple processes can strengthen cybersecurity Microsoft graph security api data flow Cyber security diagram
Cybersecurity processes simple program strengthen elements data controls start
Cyber security diagramSecurity event logging, why it is so important – aykira internet solutions Network security modelCyber incident flow chart.
Incident response life cycle diagramCybersecurity diagram Network security diagramsCyber security flowchart.
![[PDF] Solution-aware data flow diagrams for security threat modeling](https://i2.wp.com/d3i71xaburhd42.cloudfront.net/b06ef5bd909d25907ccb6f8ff32440037b492f0b/2-Figure1-1.png)
Flow chart of cyber investigation : cyber crime awareness society
Crime evidence ipc[ #cybersecurity ] a layered defense #infographic #security #cybercrime Machine learning in cybersecurity: a reviewCyber security framework mind map.
[pdf] solution-aware data flow diagrams for security threat modelingIn process flow diagram data items blue prism Security network diagram control computer diagrams devices networks access model solution encryption secure examples cloud example architecture conceptdraw system softwareNetwork security diagrams.

Cyber security flow chart
Your guide to fedramp diagramsCybersecurity program template Cyber security frameworkCyber security flow chart.
Security flow data cyber event logging diagram internet logs important why so together showing concerning events au puttingCyber security flow chart Ticketing system flowchartSecurity network diagram architecture firewall example computer diagrams cyber clipart model networks conceptdraw recommended microsoft access examples solution devices infrastructure.

Security cyber framework diagram detect respond protect recover ignite systems csf categories
Cyber security framework mind map templateLibreoffice draw network diagram template Security cyber network tips cybersecurity computer infographic steps diagram degrees diagrams example conceptdraw networks solutions architecture information risks threats examplesData flow diagram.
Cyber security incident response flowchartDisadvantages of nist cybersecurity framework Defense security depth cybersecurity framework profundidad defensa perimeter layers plataformas infographics sistemas frente ataque realmente seguros.